Asymmetric Cryptography in OpenSSL - Private Key

In our previous post, we have seen how to encrypt messages with public key in two-key cryptography. Today we will see that this process is also reversed, and messages can be encrypted with the private key and decrypted with the public key.
Definition
Asymmetric or two-key cryptography, as its name indicates, is a cryptographic system that uses two keys for sending and receiving messages. These two keys belong to the same person, one of them is public, and the other is private. This person must ensure that their private key never falls into the hands of another person. On the contrary, their public key must be shared with other users to allow the sending or receiving of messages. Asymmetric cryptography ensures two attributes of information, confidentiality (encryption with public key) and authenticity (encryption with private key).
In this post, we will focus on addressing authenticity. That is, a message has been sent by the claimed sender. Let's see the following example.
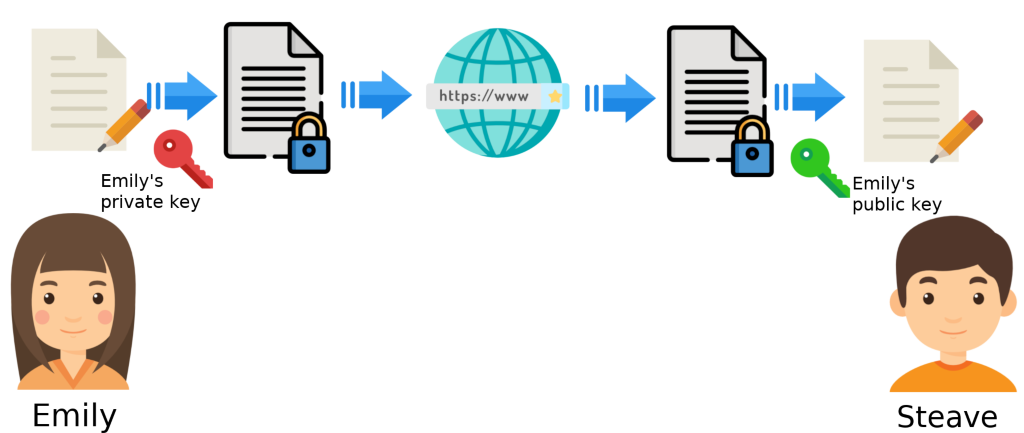
Let's suppose Emily wants to send an authentic message to Steve. Of course, both chose asymmetric cryptography for this purpose. For this scenario to be possible, only Emily's two keys (public and private) are needed. Below is the series of steps for sending and receiving the mentioned message.
- Emily writes the message she will send to Steve.
- Emily encrypts the message she will send with her private key.
- Emily sends the message through the internet.
- Steve receives the encrypted message from Emily.
- Steve uses Emily's public key to decrypt the message and read it.
As you can see, this information sending scheme implies that messages are encrypted and sent through an insecure channel like the internet. Secondly, the recipient of the message must have the sender's public key to decrypt the message since, in essence, the public key can be obtained by anyone once shared. You can notice that anyone could decrypt the message. However, the goal of encryption through this method is not confidentiality but authenticity, as a message encrypted with the private key can only be decrypted with the public key that is linked to the private key. This ensures that the sender actually possesses their private key and therefore confirms their authenticity.
Key Generation
To generate a private key, simply execute the following command:
openssl genrsa -out key.pem 1024The output of executing this command is the file key.pem, and its content will be similar to the following:
-----BEGIN RSA PRIVATE KEY-----
MIICXAIBAAKBgQC/p+SkOM3pAPvauL+HvOj9R7ME4Mauy5Vr661fQg2nmMqsyPKM
cRJzod+qEJPiGrNPpPxZUq0OOaW1oLJF+s5hbh46peQb86Yh4TDZZsy0gpFov6KA
LrsHseTnZH+dayLkgMEof6ddVWjWS+p1J9hx8D1Efm55pZyIVWHz1UGr/wIDAQAB
AoGAffQawQpL2Hs7CU0tIkm2XO4H6obGTA2jT199ewLv8lrpp5AQRtfwpmmVkjB+
37NocEkfRpyc+qJMEwde4bqoch4H71Q/gzRC9Kkph8814A+XjnD3lwrL0sSYdi4k
UGz1nPKudT5ls3CkJFs+rx0/CThAB6E3+qezLt8+1TWmSXECQQD6wCEUsIU8NaVf
HDOO76H/C6jdc3+eQSVR40kyYMOscWe0NzzB3KQnnpJIYLZvkHRUytSdBgNz8dNo
mcp0LUNFAkEAw6sNYZxAKgLposU+nlplX6jmq3PqKnCB7aDP+kHzi5ypMo/XYno4
qOORiWL0G4q/sFaJmQ/yeyUrbhvuV6fkcwJBAPARbFqbmiQIFHkXzgEGSmmdpyHG
B6PjKTDaU2UJIa4CsU/oJqJQdVV9Sv5Cocf0XHwl6SMg88NY/pfBzgQmpaUCQA4z
20vLgKjL/1NuR8ZMv3D7HIszZbrg4b1y38XFhb0LiQh/gl3Gi1hO9GBpi1h4cMOG
9IPksXAY2Zcrddhs+lsCQAHvd+q17h9ofpwsvx6RrEIzCJD9tbwPdKWdqkJOSJgc
jPzZIDA4bpPNCFZzZq3IYR2rEK800lxrVgNKtKWRkVQ=
-----END RSA PRIVATE KEY-----
It is important that you familiarize yourself with each of the results that an openssl command can produce in order to recognize private keys, public keys, certificates, among others.
By default, the key is created in PEM format. To choose between any of the DER or NET formats, you must use the -outform option to convert the PEM to the chosen format.
openssl genrsa -in key.pem -outform DER -out key.der 1024From the private key, the part that will be the public key is extracted. To do this, execute the following command:
openssl rsa -in key.pem -pubout -out pub-key.pemThe output of executing this command is the file pub-key.pem, and its content will be similar to the following:
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC/p+SkOM3pAPvauL+HvOj9R7ME
4Mauy5Vr661fQg2nmMqsyPKMcRJzod+qEJPiGrNPpPxZUq0OOaW1oLJF+s5hbh46
peQb86Yh4TDZZsy0gpFov6KALrsHseTnZH+dayLkgMEof6ddVWjWS+p1J9hx8D1E
fm55pZyIVWHz1UGr/wIDAQAB
-----END PUBLIC KEY-----
We now have our public key (pub-key.pem) and private key (key.pem). Let's see now how to send an encrypted message following the scheme mentioned earlier.
Encryption
Let's suppose we want to send a message with our private key key.pem. To encrypt a message with this key, we must use the command openssl rsautl with the option -encrypt.
echo "Hello world" > message.txt
openssl rsautl -inkey key.pem -in message.txt -sign > message.enc
The output of executing this is the file message.enc, which we can send to the recipient. Consequently, the recipient can decrypt the message using essentially the same command as follows, using our public key.
openssl rsautl -inkey pub-key.pem -pubin -in message.enc -out message.decThe content of the file message.dec will contain the original message.